Avoid Viruses Phishing Spam
How To Avoid Recent Common Malware Techniques
This article shows you how to avoid viruses phishing & spam. When it comes to online security, It is very easy to get your information stolen online without having to download anything. The new methods of hacking can infect you without any alert, prompt or even being seen by a naked eye. Getting your computer infected by downloading a file attached with an email and stupidly double click on it to get hit by a virus. You may have laughed at someone before for this but these days; hackers are getting so smart and resort to new techniques to lure their bait to the fish line. After reading this article, I assure you that you will be putting your hands covering your mouth and Oh My Gosh, I fell for this as well.
Recently, a lot of gamers have their gaming accounts hijacked. This is because a lot of gamers choose to drop their anti-virus or protection software while gaming just to reduce the drop in performance. As a result, the system opens the door to hackers. Most of us get hit by malware these days in the form of drive-by download. You can get hit even by visiting safe sites. Most of these infections can enter a system easily in the form of ads that we see online. Flash ads will require the browser to download some files to the computer and execute them. One of the files may be the malware and as the advertisement is showing on screen, the malware can already be executed.
Here are some of the latest security threats used in online frauds
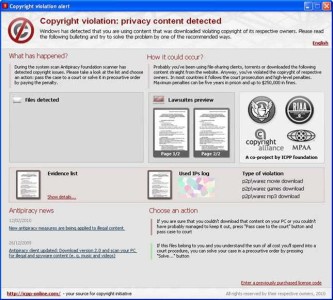
1. Pirated content warning
This is similar to scareware where by users are presented with an ad that claims that they are heavily infected with viruses. So, if you are really doing an illegal download on a website that actually provides such services, you will be presented with a pop up that says, Copyright Violation: Copyrighted Content Detected
You are informed that the information collected on your illegal files will be passed to the courts for appropriate lawsuits.
Click for larger image
A way to settle it out of courts will be offered to you; click on a link for a settlement by paying a fee of USD $399.85. [ Most major credit cards accepted ]
This warning looks very real with all the logos of copyright associations of America Motion Pictures. But it is just a total scam.
2. Devices flashed with malware code
It is possible to embed malware code inside a device like thumb drives or Mp3 players. Most portable devices contain a flash memory that allows storage of program files so that the device can run on its own. You can find many budget devices that are not from a reputable company. These are the ones that can include malware and it is impossible to disinfect the device since it is hard flashed into a ROM.
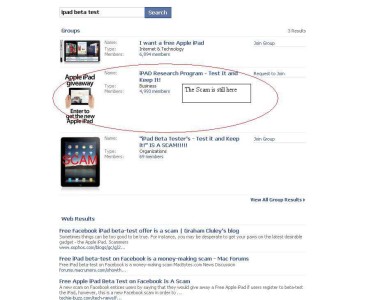
3. Freebies as bait
Hackers love to use free gadgets as a form of trick to extract information from users. The most recent one being used is the idea of looking for iPad beta testers. Use the iPad for 2 months and provide feedback and you get to keep it. This scam is even running wild in Twitter and Facebook.
Click for larger image
What happens is that before you are able to join the beta test, you will need to key in your personal particulars so that they can enter you for the trial. Once you have submitted all your information, they will most probably ask you to wait for further notice and details of collection of the iPad where you will be left waiting and waiting. You have already lost your private information to scammers
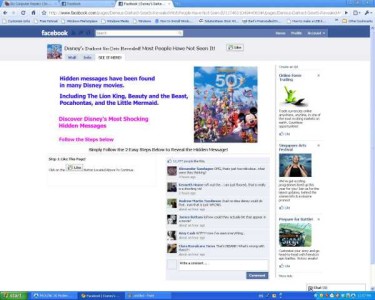
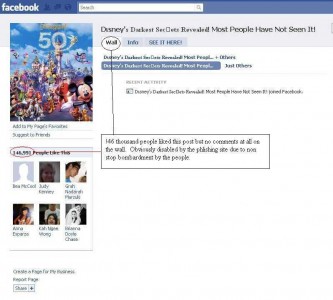
4. Shortcut to a site that is malicious.
The web is able to reduce a lengthy URL to a shorter one. Hackers love to create a URL that looks legit in the first few words but actually the whole URL links to somewhere else which will give the game away. So unknown to users who think that the URL is not harmful, will click on it and land on a site that sends malware to the computer.
Click for larger image
Click for larger image
Click here for proof that this site is nothing but scam and dangerous
Always exercise caution. Hold your mouse over the URL before clicking on it to check if the site is harmful. If unsure, right click on a link and select “copy link address”. Then go to McAfee SiteAdvisor to check the link first.
Cyber crime is not an act of just an individual; it is more of a bunch of people working with one another because they need each others services. Here’s the breakdown of the online terrorists.
1. The Phisherman
This type of person is a genius at creating websites. They can do up one entirely new website which looks like a replicate of the genuine site, it looks identical from the way the site is organized to the colors being used to even the contents from the site. I once visited a fake bank phlishing site that even has the same flash advertisement shown on the real site. Except that the URL is different. Once you key in your login credentials on this fake site, you will most probably be led to a page that says that the site is undergoing some server upgrade or maintenance. Actually, he has already gotten hold of your login and password.
2. Bot Herder
These types of hackers are those who will manage and keep track of computers that have already been compromised and infected. He is able to gain control of a huge arsenal of computers and remotely execute instructions for infected systems to start bot net attacks on their targets. One common method would be to get all the infected systems to land on a website and create stress on the network and thus bringing down the site.
3. The Businessman
A business man is as harmless as anyone of us, but in order for his business to attain greater heights, he may resort to hiring of bot herders and malware writers to bring down the website of his competitors. He can also use the services of spammers to advertise his product more commonly known as the spam mail in our inbox.
4. Writer
A writer is not the journalist that we know of but the smart techies that can write new malware and Trojans. They will release newer updates and patches to avoid being detected by scanners and anti-virus.
5. Spammers
Spammers may look useless as they only post a certain message or text all over the net or send tons of emails. But a spammers job is not that simple, they will need to observe and monitor the net for the latest discussions and trends, by posting messages about the latest hot topic, curious users will be tempted to click on that link and ends up falling to the drive-by download when they land on a infected site or ends up entering details into a phishing site since some of the techniques used are for the user to key in their login for a certain account in order to view a video or something.
Here are some of the most commom malware that exist on the internet that you should be careful about.
1. Drive-by download
Any website can have infections, even a trusted page can be compromised and when you visit the website you will download malware without you even knowing. It works through the flaws of the browser and so it is important that you keep Web browser updated.
2. Screenscraper
This is the advance version of a keylogger which records what you type on screen, but we all know that you can get past a keylogger by using the onscreen keyboard. But a screenscraper records whatever is on screen like a camcorder.
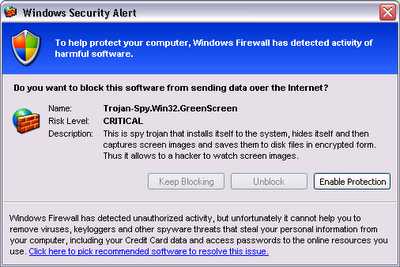
3. Scareware
A scareware is one of the lowest form of malware that works on the principle of fear. It shows up like pop up ads. But it is designed in a very clever manner that looks like a real warning claming that the user’s computer is full of infections. It usually comes with a purchase on the fly solution. Once you make payment, you will only buy some bogus software that does nothing more than display a message saying that the threats are fixed.
This is one example of a scareware that is very well designed to look like a Windows alert in any way. Except for one thing. A cross at the top right corner. This gives the game away since only browsers or a Window has that cross. So if you are unsure what to do next, click on the cross and not “Enable Protection”, because that will allow the malware to install itself onto your computer.
4. Bundling of malware code with a program
Getting program registered by means of using key generators is one convenient way to get free programs without paying. But these generators could come with malware that will steal your information, since in this world there is no free lunch.
5. Rootkit
Think Rootkits as a weapon, alone it is harmless, but when someone picks it up and starts firing, it will do a great deal of damage. Rootkits are actually software designed to gain administrative privileges. For example, a rootkit file is downloaded into the drive and it lands somewhere. You click on a advertisement or a flash game, it actually executes a command to replicate this file somewhere in the harddisk near the boot records. This is because there is always some free space before the start of the Operating System which is not reflected when you check your drive space. So this is a good place for the rootkit to stay hidden when it is not in use. When you click on a fake warning or start a malicious executable, this is where the mal-program can take control of the rootkit and gain administrative rights.
After reading this article, I hope all of you will be able to avoid viruses and Phishing scams with fake warnings and protect yourself from being infected by malware. It is not up to the protection software to protect you if you do not exercise caution and fall prey to such tactics.
2 Comments Already
Leave a Reply
You must be logged in to post a comment.

Thanks a lot for this useful articles, i often have a virus in my computer, don’t know at all where do they come and i always mustreinstall the computer, it is really annoying, hopefully, antivirus softwares exists but sometimes it fail to find the virus…
Yes the big problem is that virtually everybody protects against virus infection, yet 90% of malware infections these days are from Trojans & the cheaper or free antivirus programs are not designed to detect or deal with trojans.
I would recommend you invest in a very good anti spyware program like Spyware Doctor as I have not yet found a Trojan infection that it has failed to detect or deal with !